
Clustering R&I Initiatives
Clustering Cybersecurity and Privacy Excellence in Europe
An overarching goal of cyberwatching.eu is accelerating development and deployment of cybersecurity & privacy research results, thereby increasing Europe’s ability to design and deliver innovative solutions. Research and Innovation (R&I) projects have spearheaded across the EU & Associated Countries (ACs) on the development of novel architectures and technologies, which can protect our European Digital Society against cybersecurity & privacy threats, although they may not gain the necessary visibility to generate impact.
Who will be clustered?
cyberwatching.eu is performing a comprehensive observation of national and pan-European R&I initiatives, standards, policy & regulation, and market needs. cyberwatching.eu will provide a platform for fostering project collaboration, through a two-stage clustering of projects, thereby allowing cross pollination of both non-technical policy, experience and best practice findings as well as deeper technical specifics bringing expertise from across the top-level cluster together to concentrate on specific issues in smaller and more tightly focused groups.
How will projects be clustered
As a first meta-clustering to bring together those projects, three specific high-level cluster definitions have been created:
|
1. Foundational technical methods & risk management for trustworthy systems in cybersecurity & privacy: The development of technologies that are directly associated with cybersecurity capabilities or features and methods by which the confidence in the technical capabilities of a system may be validated. 2. Applications and user-oriented services to support cybersecurity and privacy: Specific capabilities or services which directly interact with system users and are developed with capabilities that are directly about how to improve the inherent capabilities and user experiences of cybersecurity and privacy in consumed services. 3. Policy, governance, ethics, trust, and usability, human aspects of cybersecurity & privacy: Aspects of cyber security that are overwhelmingly driven by the human interaction, understanding and dependency on how secure systems are or have been designed to be. |
Already 150 CS&P projects have been analysed according to these definitions with a full catalogue and up to date service offers provided for 48 ongoing projects which will be presented at this month's Concertation meeting.
These clusters of projects will form the basis for identifying:
- Future collaboration and sharing of experience on common technical priorities;
- Re-use of project results with components, technical ideas, methodologies or best practices identified by a repeatable statistical analysis rather than qualitative methodologies;
- Identify market positioning and potential exploitation opportunities with other projects.
As a next step,
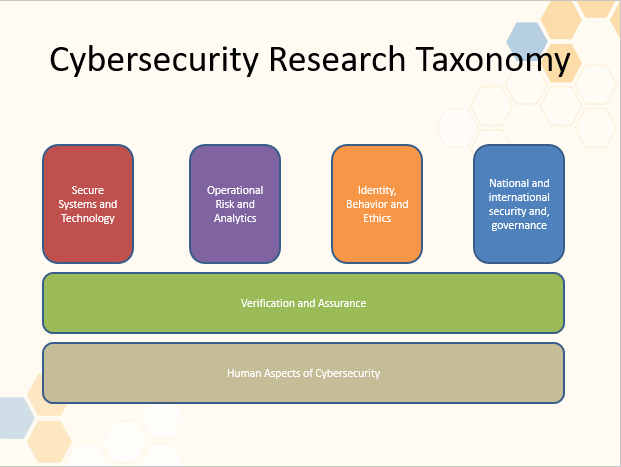
Secure systems and technology
- How security can be built into technology from the design stage including cloud computing security, cryptography, trusted platforms, wireless security, mobile security and secure coding paradigms.
Verification and assurance
- Two disciplines that help establish how much confidence you can have in a system, both in terms of security and the privacy of all stakeholder groups who act with or in a system. Assurance focuses on managing risks related to the use, processing, storage, and transmission of information, whereas formal verification seeks to build a mathematical model of a digital system and then try to prove whether it is ‘correct’, often helping to find subtle flaws.
Operational risk, management and analytics
- Developing understanding of risk and harm resulting from cyberattack
- Cyberattack propagation across and between organisation
- Awareness of current understanding of scenario and risk management
- Metruics and models for security postures
- Analytics for predicting risk, prioritising responses and supporting security operations
Identity, behaviour, ethics and Privacy
- Management of personal identity including different levels of assurance when used for online capabilities or services
- How to understand common norms when applied in the online or digital realm.
- Diverse perspective and interpretations to questions such as: Who are you online with? How do you communicate and what can (or should) you do? What expectations (personally and legally bindings) are there?
- Whay expectations of privacy can there be and should there be?
National and international security, privacy and governance
- Development of politics, international relations, defence, policy and governance issues.
- How do countries and communities interact with (and through) technology, and how might this change in different contexts?
- How do national standards transcend borders or boundaries?
- How should different threat persistence levels and domain cybersucurity understanding should be shared?
- At what point does something change from being a business problem to a national security problem.
Human aspects of cybersecurity
- Understanding human interaction with (and through) digital systems (whether to understand and design for target users adn to better understand how adversaries operate anc can exploit the system).
- Include aspects like usability, trust, collaborative practices, social embeddedness, nationhood, cultural diversity and the relationship between microsocial interactions and global structures.
News
On the event of the adoption of the draft regulation laying down measures for a high common level of cybersecurity at the institutions, bodies, offices and agencies of the Union, the AI4HealthSec project kicked off a process to provide its opinion.
Resources for EU Research
Resources for SMEs
News & Events
Reports
Cyberwatching.eu has received funding from the European Union’s Horizon 2020 research and innovation programme under grant agreement No 740129. The content of this website does not represent the opinion of the European Commission, and the European Commission is not responsible for any use that might be made of such content. Privacy Policy | Disclaimer / Terms and Conditions of Use
